When preparing for the
CCNA exam, review routers and their protocols by starting with the difference between a routed protocol and a routing protocol. Knowing the difference between these two protocols is fundamental to understanding how routers route.
Networked devices communicate over routes, which are paths between sending devices and receiving devices. A networked device learns about a route between it and another device in a variety of ways:
- Manually: A network administrator can manually configure a route.
- Pull: Devices can send out polling messages or "probes" to discover the route to a destination.
- Push: Devices can send out route information about routes it knows.
Regardless whether the route information is manually entered, discovered, or received from another device, the information learned is stored in the routing table for later use.
Inside versus outside
A routing
protocol sends and receives routing information packets to and from other routers. A routed protocol can be routed by a router, which means that it can be forwarded from one router to another. Yes, there are protocols that can't be routed, such as NetBEUI (Network Basic Input Output System Extended User Interface).
That a routed protocol can be routed may seem obvious, but unless you know how to differentiate it from a routing protocol, you may have trouble with the wording for some questions on the exam.
A protocol is a set of rules that defines how two devices communicate with one another. It also defines the format for the packets used to transmit data over communications lines. A routed protocolcontains the data elements required for a packet to be sent outside its host network or network segment. In other words, a routed protocol can be routed. Protocols used to communicate routing information between routers within an autonomous system are Interior Gateway Protocols (IGP), which are routing protocols, but not routed protocols.
Routing protocols gather and share the routing information used to maintain and update routing tables. That routing information is in turn used to route a routed protocol to its final destination. Routing Information Protocol (RIP) and Interior Gateway Routing Protocol (IGRP) are the routing protocols you need to know for the exam. If you can remember what the abbreviations mean, you'll remember that they are routing protocols because they have routing in their names. Remember, too, that they are not routed protocols.
In short, routed protocols route your data and routing protocols send routing updates between routers about the status of the network so that your routed protocol data can be routed. Got that? No? Well, try this to help keep it straight:
1. Routed protocols get routed.
2. Routing protocols are for updating (the info about the routes over which routed protocols are routed).
Examples of routed protocols are IP and IPX, and examples of routing protocols are RIP and IGRP.
A routing we will go
Routing is the process of moving data along a path from a source to a destination. The complexity of this process involves finding the most efficient route from a multitude of available routes. Routing occurs at the Network layer (Layer 3).
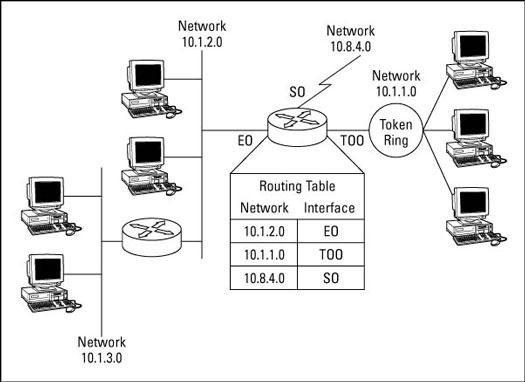
To assist itself in making its routing decisions, the router builds routing tables to store information about routes to networks it has previously discovered. Most routers keep an entry, known as the default route, in their table to be used when the router doesn't have an explicit route for a packet. Figure 1 shows both what a routing table contains as well as where it fits into a network. Notice that it consists of network addresses and the interface to which each device, associated with an address, is connected.
Figure 1: A routing table of a network router.
Routing types you need to know for the exam
As far as the CCNA exam goes, there are three types of routing: static, dynamic, and default. Details about these routing types appear in the following sections.
Static routes: One-lane roads
Static routes are fixed routes that are manually entered by the administrator into the router's configuration. If a static route is entered into the configuration, it must be manually updated should the network topology change. Not that the topology of the network is likely to change too frequently, but you may decide to change the segmenting structure or make other topology-level changes. When changes occur, the administrator must update the router configuration to include the changes, which is why static routing is not generally used in a large network. The time required to maintain the routing tables can become a burden.
Static routes are generally used if the internetwork, the part of the network that lies beyond the router, is accessible through only one path. A network with only a single path to the rest of the internetwork is known as a stub network. Static routes are also used for security reasons because they allow the administrator to restrict knowledge of the network from outside sources. A static route is configured on the router with a command like this:
Router(config)#ip route 192.168.1.0 255.255.255.0 192.168.101.1 3
This example contains the command (ip route) and the IP address of the destination network, the subnet mask, the IP address of the next hop router, and an administrative distance (more on that later).
Using the previous command example, the key elements of the static route configuration command are (memorize these for the exam):
- ip route: This is the command used to designate a static route.
- destination address: In this example, 192.168.1.0 is the IP address of the destination network.
- subnet mask: 192.168.1.0 is a Class C IP address and is using the default subnet mask for Class C addresses, 255.255.255.0.
- next hop: Following the subnet mask is the address of the next hop router, 192.168.1.1.
- administrative distance: This is a number between 0 and 255 that indicates how well the route can be trusted. The higher the number, the lower the trust. An administrative distance of 120 falls about midrange on the trustworthiness scale. So, as indicated by the 3 in the ip route command, this route is very trustworthy.
A dynamic personality
Dynamic routing is the process by which a network adapts automatically to the changes in topology or traffic as those changes occur. To be successful, dynamic routing requires timely maintenance of routing tables. The routing protocol used defines how this occurs and includes such information as when, what, and how the updates are sent.
When all else fails
A default route is very much like a static route. The administrator enters the default route, and it becomes the default path the router uses to forward packets for which it knows no other route to use. Without a default route, packets with unknown destinations are dropped.
When no specific next hop is listed in the routing table for a particular type of packet, the router uses its default route, a preassigned route that is generally available.